1 Introduction to the Solution
In order to detect various failure states in information exchange, AUTOSAR puts forward the E2E mechanism, which adds DataID, CRC, Counter and other control fields to the communication data, so that the software can detect and deal with communication link failures at runtime. E2E protection enables:
1) Security related data elements to be sent via RTE are protected by additional control data.
2) Verify security related data elements received from RTE through control data.
3) When an error occurs in the received security-related data element, a notification can be issued and processed by the relevant SWC.
With the development of the automotive industry, the complexity of the design of automotive electronic products, especially the complexity of software development, has also been greatly improved, and the industry has paid more and more attention to Safety. ZC Technology has many years of experience in controller development in line with ISO 26262 functional safety requirements, and has established strategic partnerships with well-known domestic automotive companies.
To meet the ISO 26262 functional safety requirements in the process of pain point - E2E specific project implementation, ZC technology provides the corresponding solution.
E2E protection is the cornerstone of communication security for critical systems and can effectively address multiple risks during data transmission and processing,the common E2E protection schemes are as follows:
Ø CRC check + counter:
n Cyclic Redundancy Check (CRC) is used to verify data integrity
n Add counters to detect data freshness (prevent replay attacks)
n Simple to implement and suitable for most ASIL B-D applications
Ø Security protocols (such as AUTOSAR E2E):
n E2E protected library defined by AUTOSAR standard
n Various profiles (such as Profile1-5, etc.) are available for different ASIL levels
n Includes data ID, counter, CRC and other mechanisms
n Multiple Profile variants available (e.g., Profile1A 1B 1C, etc.)
Ø A failure state that can be detected:
n Repetitionof information:The message is received more than once
n Loss of information:The information or part of the information is deleted from the transmitted information flow
n Delay of information:The message received was later than expected
n Insertionof information:Inserts additional information into the transmitted information stream
n Masquerading:Inauthentic information is accepted by the recipient as true information
n Incorrect addressing:The message was sent from the wrong sender or received by the wrong receiver
n Incorrect sequence of information:Modify the order of information in the transmission flow
n Corruption of information:Information is changed content
n Asymmetric information sent from a sender to multiple receivers:Multiple receivers receive different messages from the same sender
n Information from a sender received by only a subset of the receivers:Some recipients did not receive the message
n Blocking access to a communication channel):Access to the communication channel is blocked
Secure Update ensures that only authorized software can be used by the controller, and when paired with Secure Boot, it can effectively prevent the execution of unofficial programs by the controller.
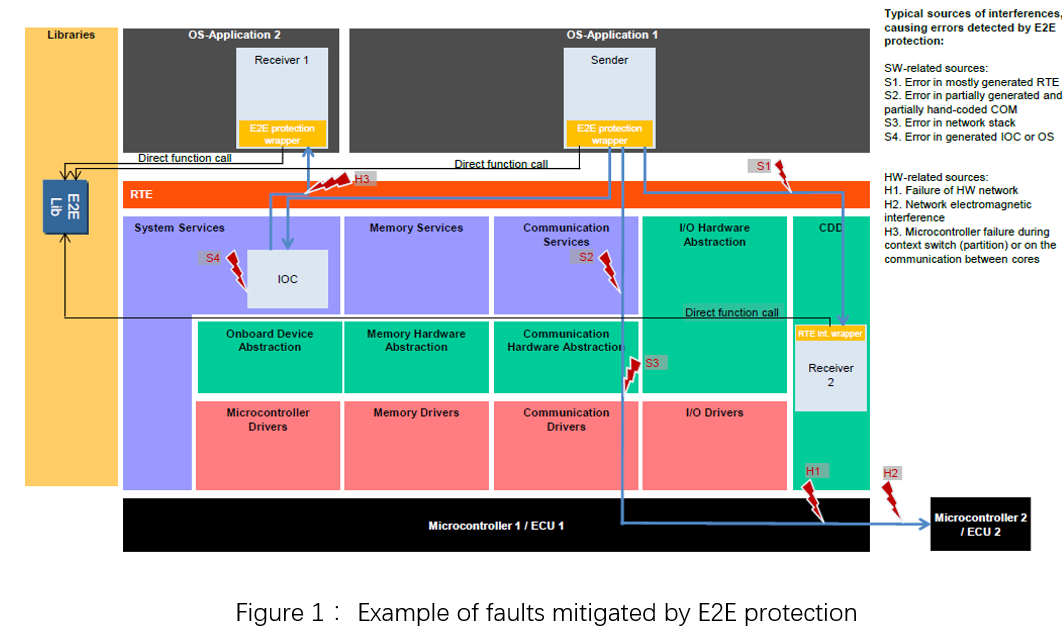
2 E2E Applications

ZC Technology can provide customers with a complete E2E solution, and can be customized for the specific needs of the project:
l Communication protection scheme based on CAN/CANFD/LIN/ FlexRay
l Communication protection scheme based on UART/SPI etc
l Communication protection scheme based on ETH
3 ZC.MuNiu E2E SafetyLibrary
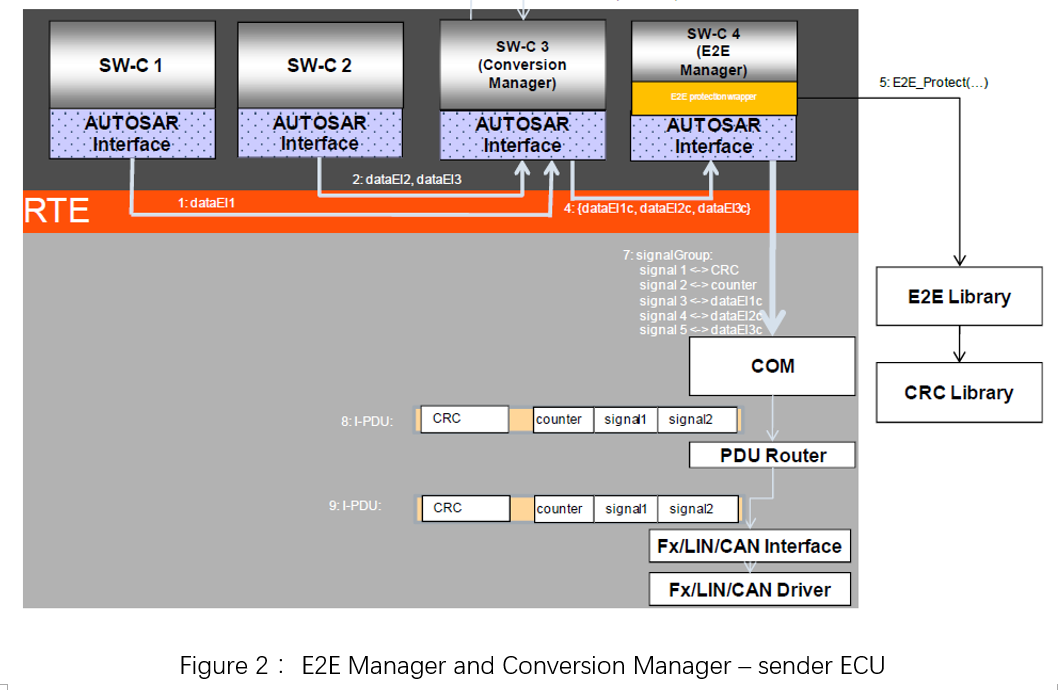
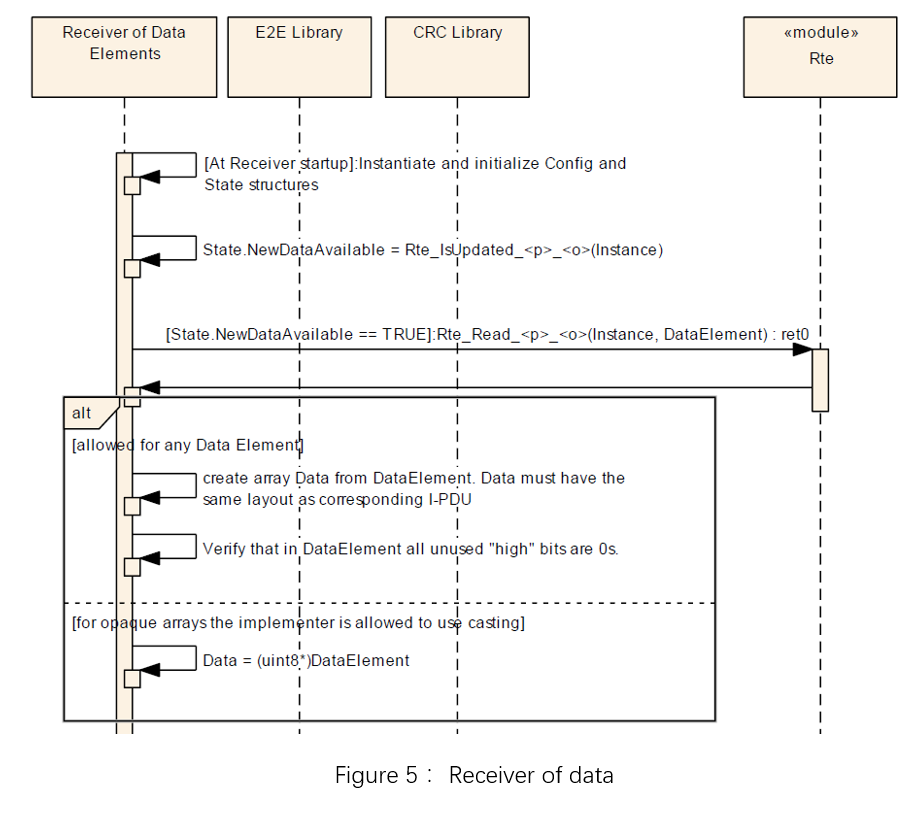
3.1 E2E Protocol Stack
The E2E stack is mainly composed of E2E and CRC modules. The E2E module is configured to implement the communication protection required by the user, etc., and calls the interface to send or receive. The CRC module performs CRC operations for the E2E module and obtains specific CRC results. 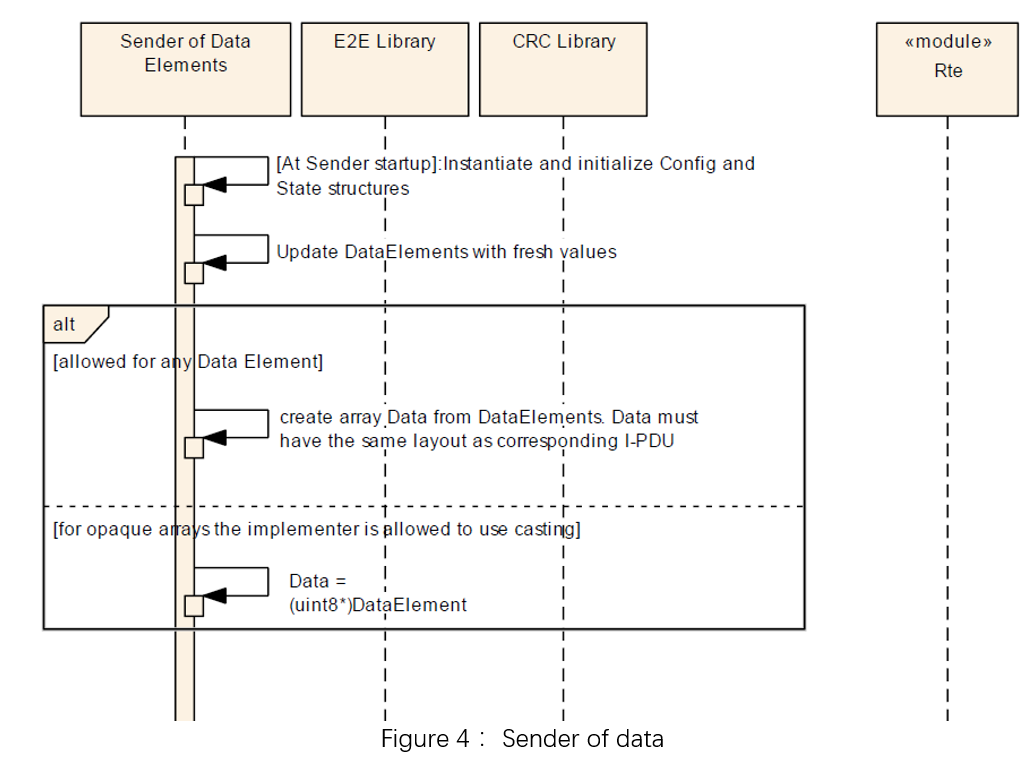
4 CERTIFICATE


