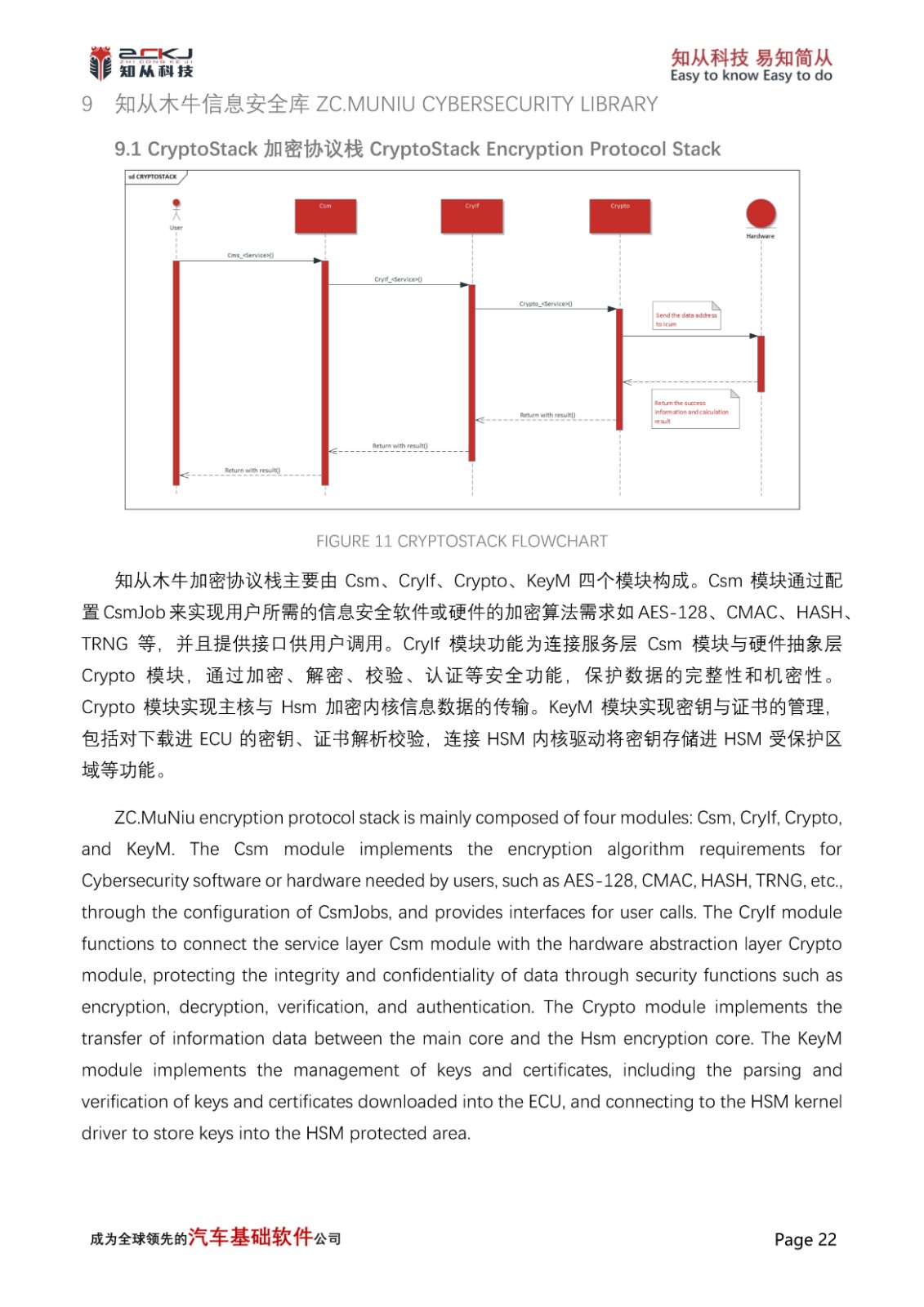
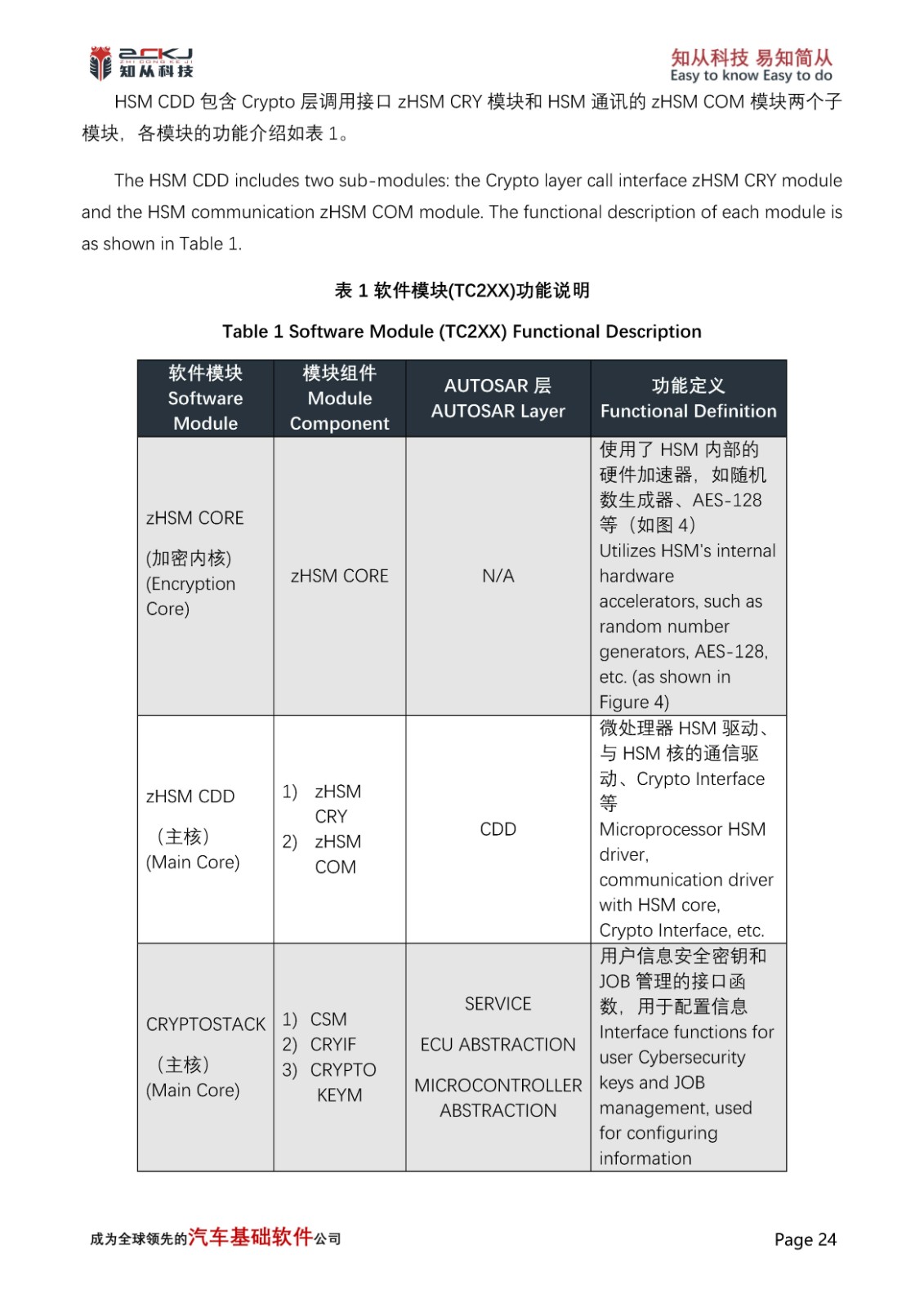
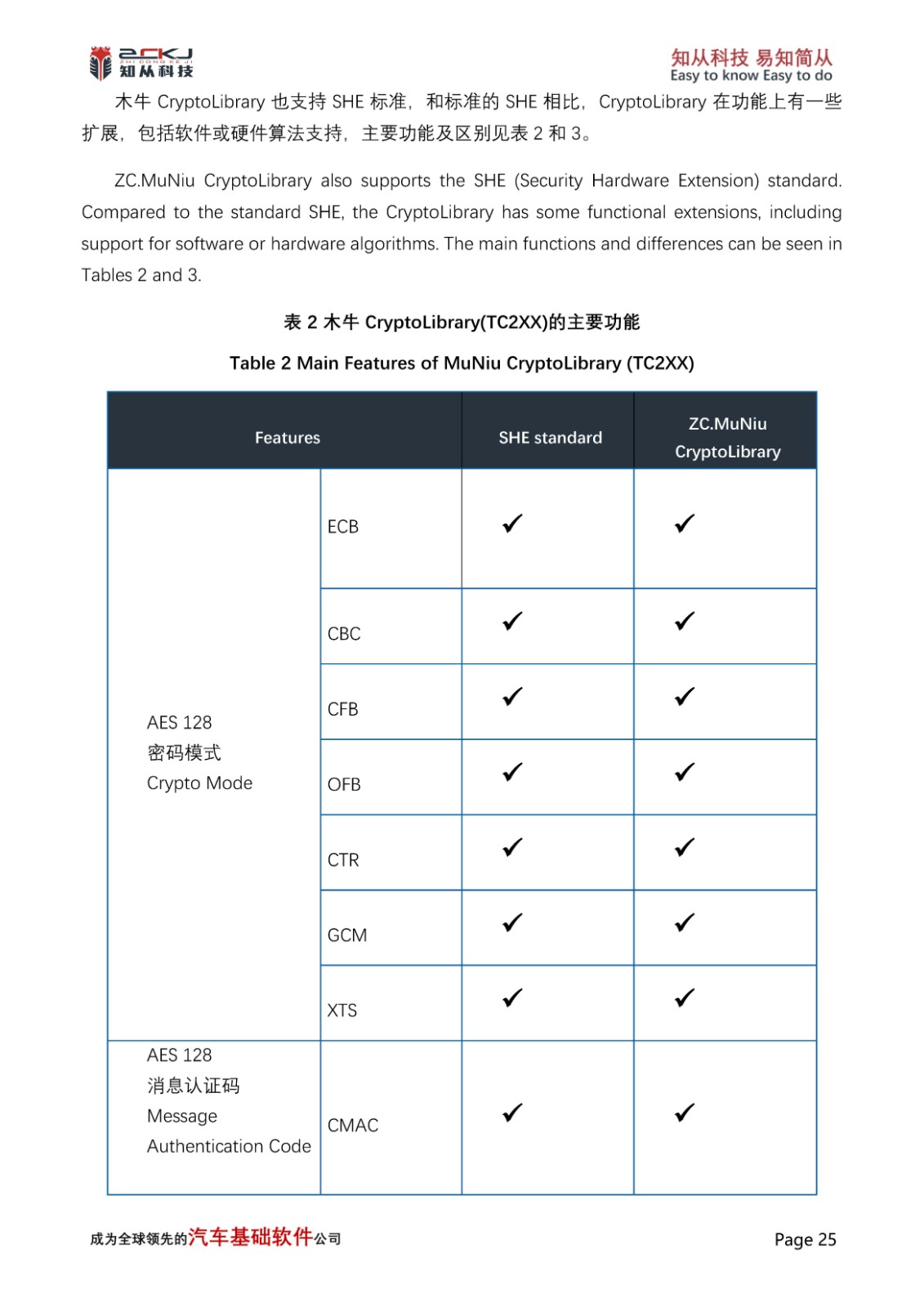
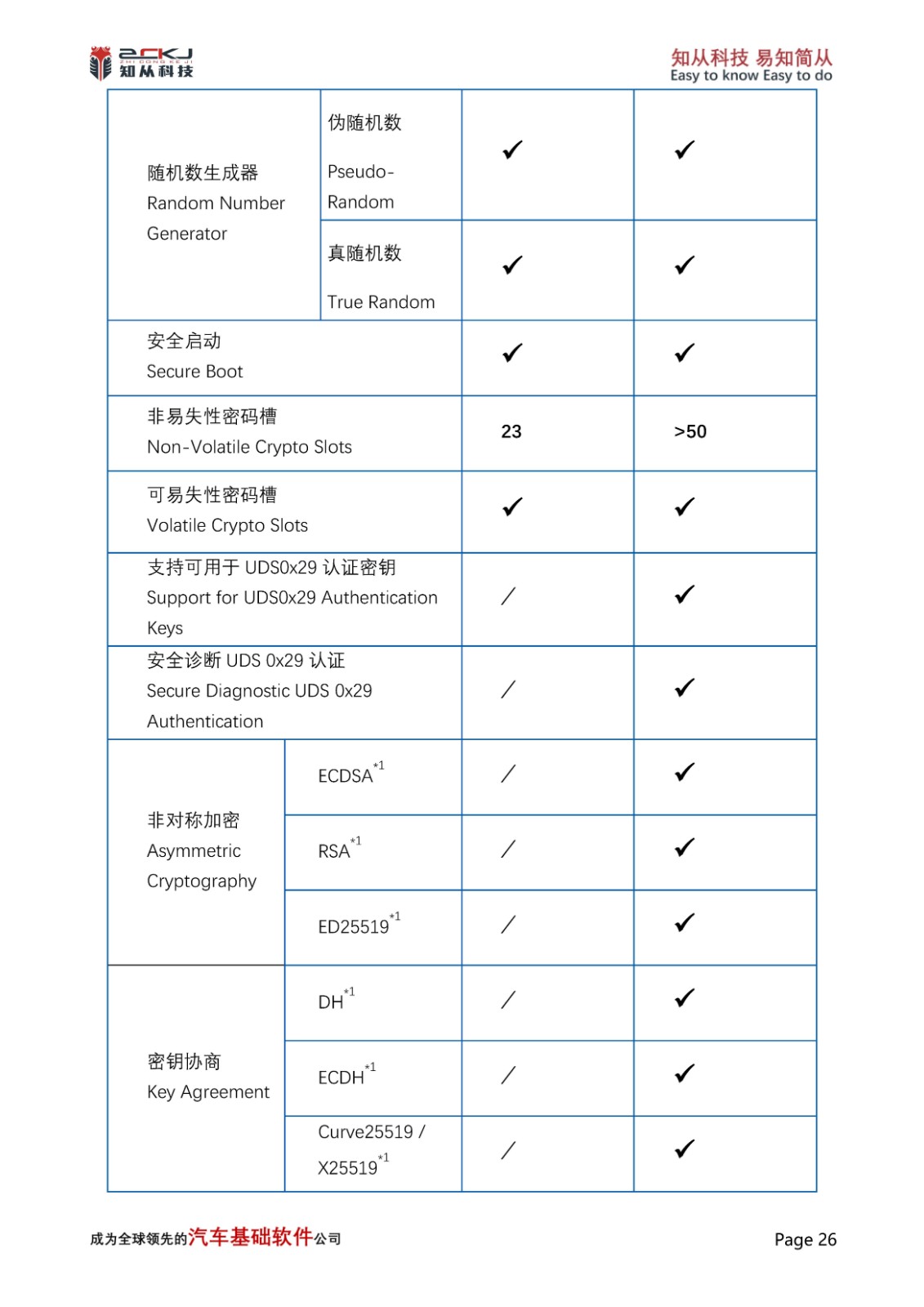
1 Introduction of CYT4BB and CyberSecurity Applications
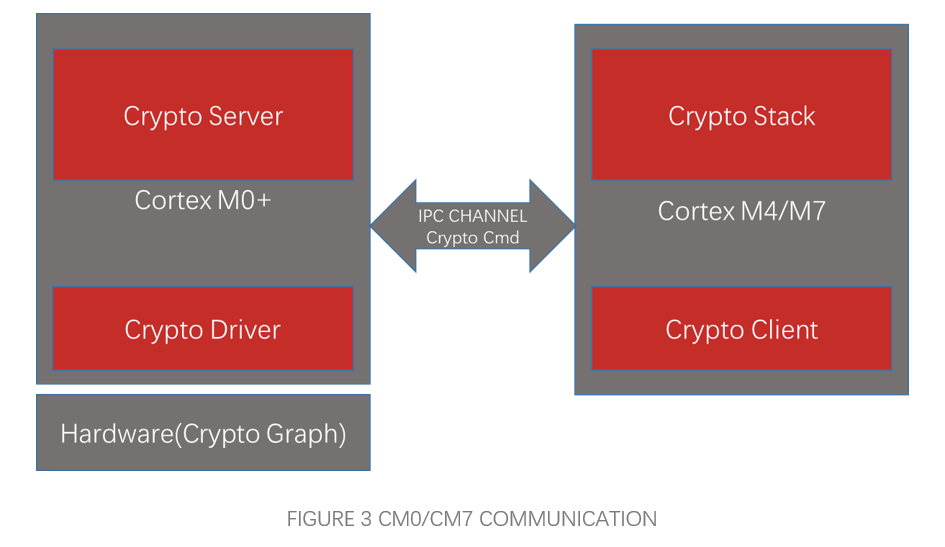
CYT4BB TRAVEO™ T2G 32-bit automotive MCU is targeted at automotive systems such as high-end body control units.The CYT4BB features two Arm® Cortex®-M7 CPUs (for main processing) and one Arm Cortex-M0+ CPU (for peripheral and security processing). Among them, the CM0 core integrates a variety of hardware algorithm functions, including: AES, CHACHA, CMAC, CRC, DES/TDES, SHA1/SHA2/SHA3, HMAC, TRNG/PRNG, RSA, and many other algorithms, based on which it can be implemented to extend a variety of information security applications, such as: SecureBoot, SecurUpdate, SecureDiagnostics other functions.
In addition, ZC Muniu CryptoLibrary integrates a variety of software algorithms and extended applications based on the original hardware algorithm function, such as: SM2/SM3/SM4, ECDSA 256R1, RSASSA-PKCS-v1_5(4096bits Key), RSASSA-PSS-(4096bits Key), SHE/ USERKEY Load, GetUid, KDF, DebugHandling, etc., to achieve secure storage.

1.1 Communication Feature
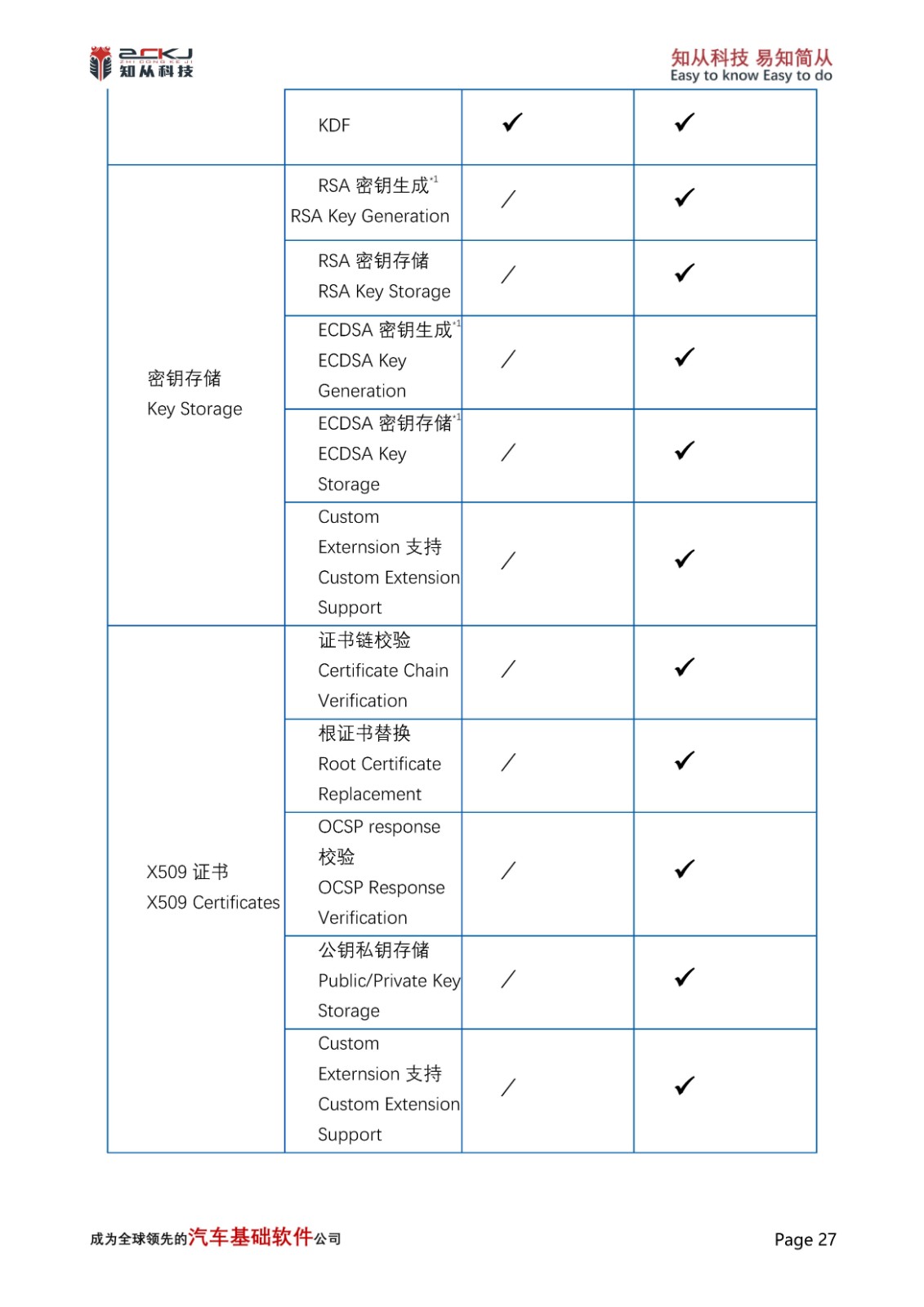
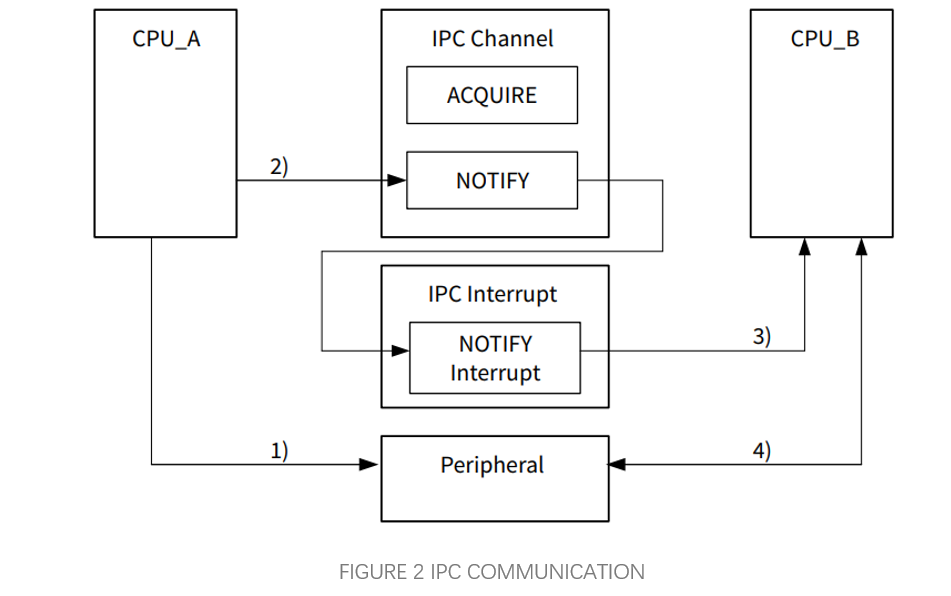
The IPC hardware contains register structures for IPC channel and IPC interrupt. IPC channel registers implement lock/release mechanisms, and messaging. IPC interrupt structure registers generate interrupts to each CPU for messaging events and lock/release events.The IPC channel structure ACQUIRE register provides lock feature and IPC_STRUCTx_LOCK_STATUS indicates lock status. The IPC_STRUCTx_NOTIFY register generates notification event, the IPC_STRUCTx_RELEASE register releases IPC channel structure and generates release event.
After the CM0 core releases the CM7 core through secure boot, the CM7 calls IPC channel and interrupt initialisation, and calls Cy_Crypto_Enable to notify the CM7 core to initialise the IPC channel and related interrupts. When both initialisations are complete, other algorithmic tasks can be invoked for processing.
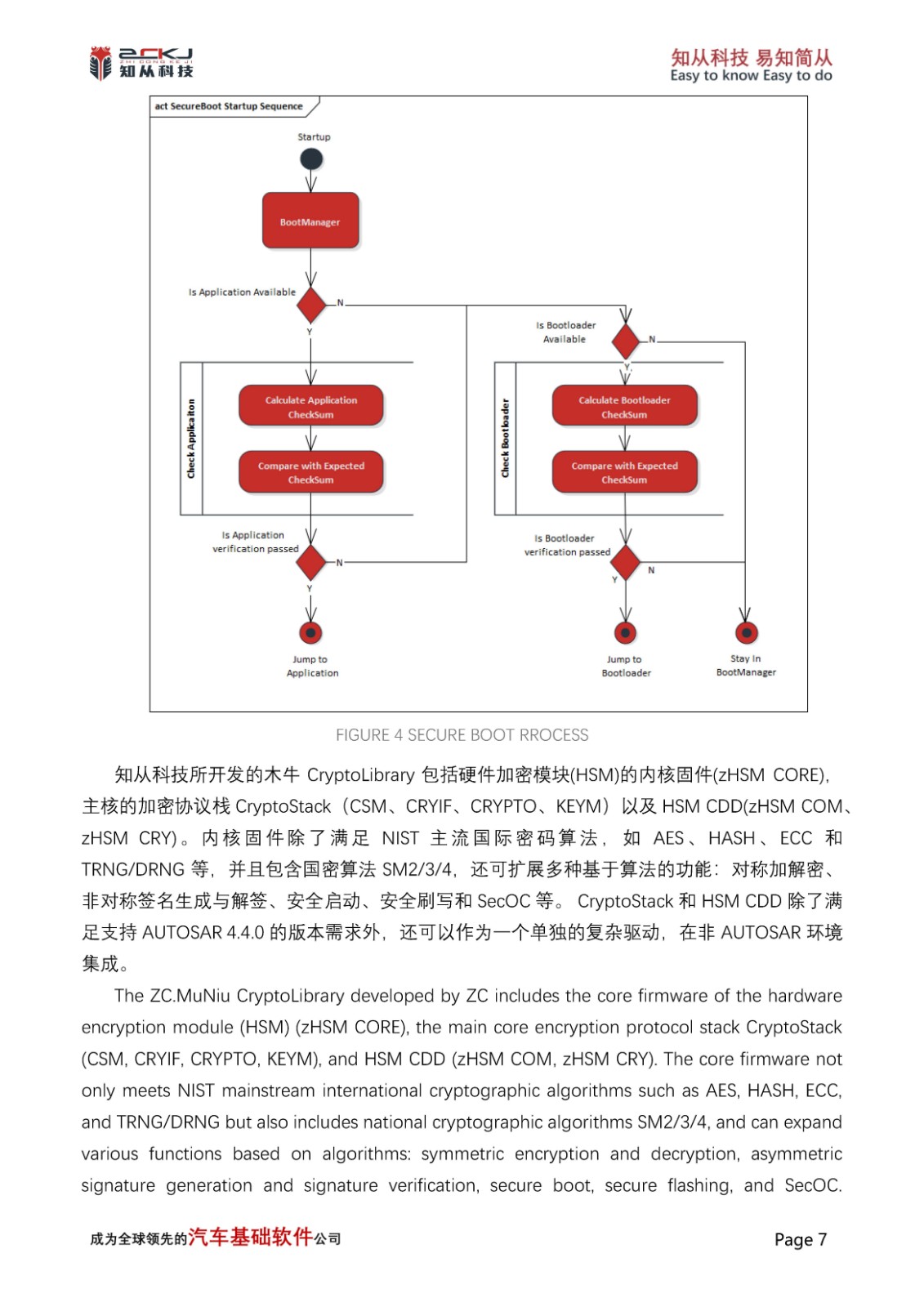
2 Secure Boot
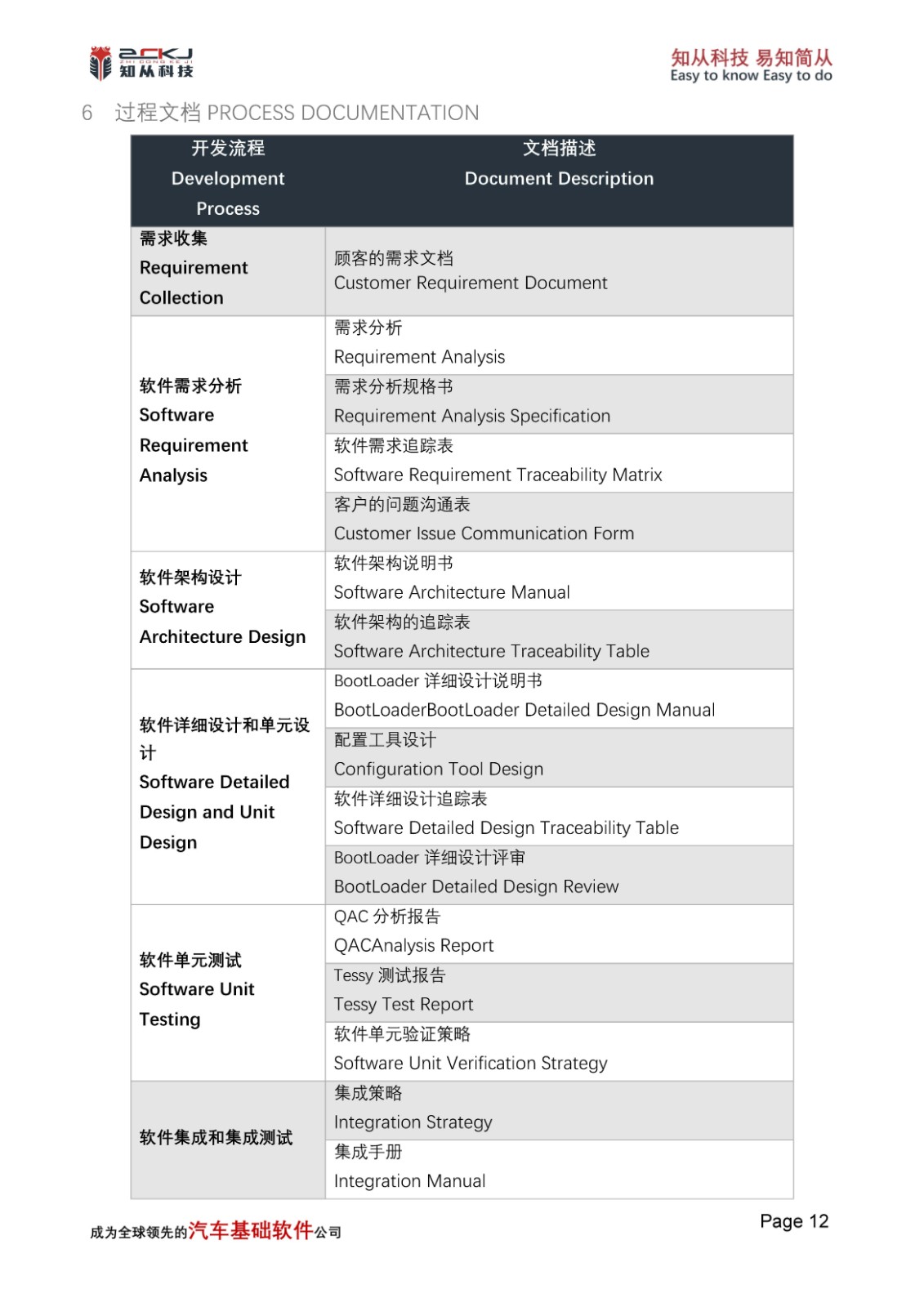
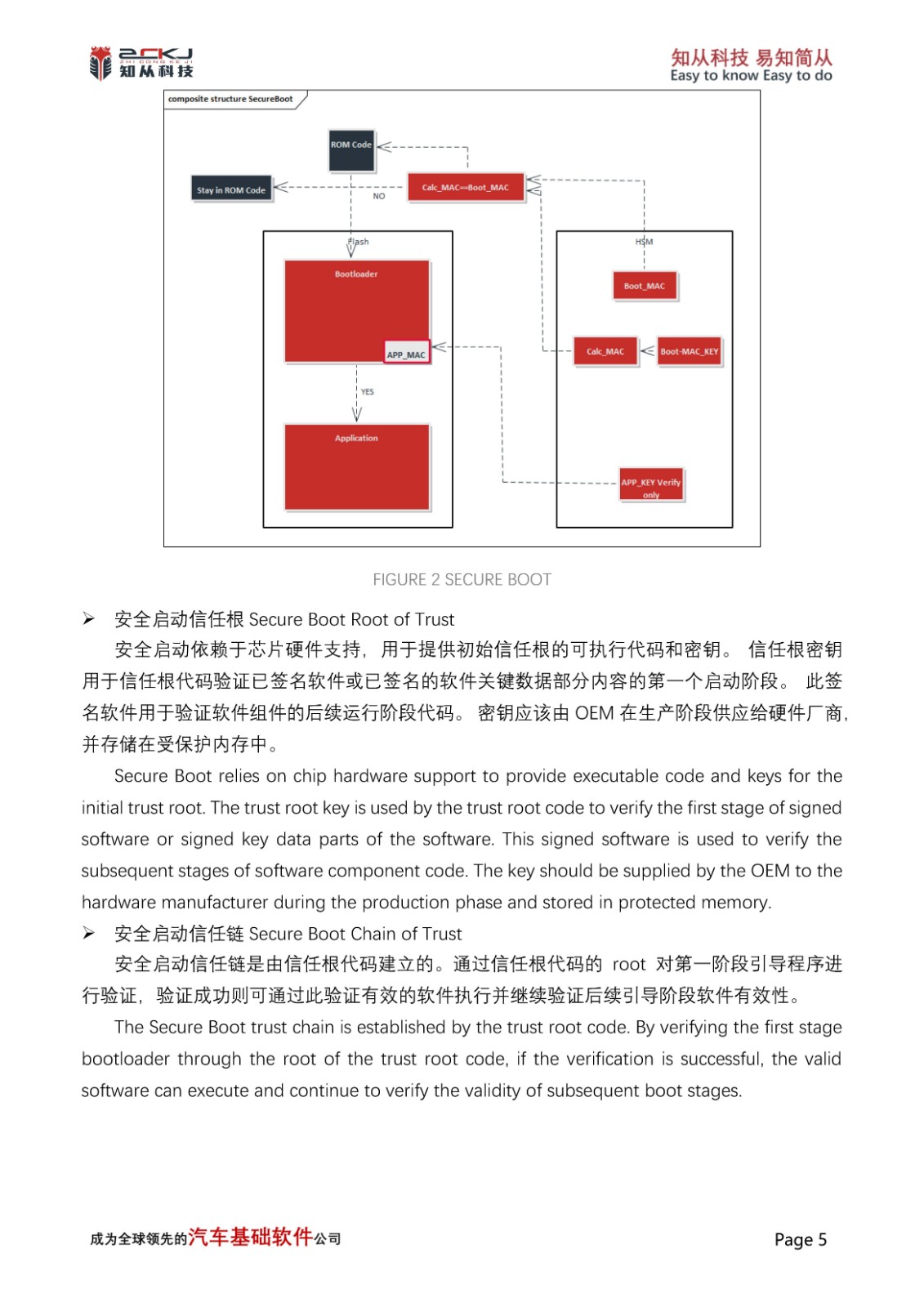
Secure Boot is a fundamental function of the MCU, implemented through hardware encryption modules. This mechanism must operate independently of user programs and cannot be compromised. As the foundation of the entire secure boot trust chain, Secure Boot is mainly used to verify the integrity and authenticity of key programs defined by users in Flash memory after the MCU starts and before user programs execute, to determine if they have been tampered with. If the verification fails, it indicates that the MCU is in an untrusted state, and some functions or even the entire program cannot run.
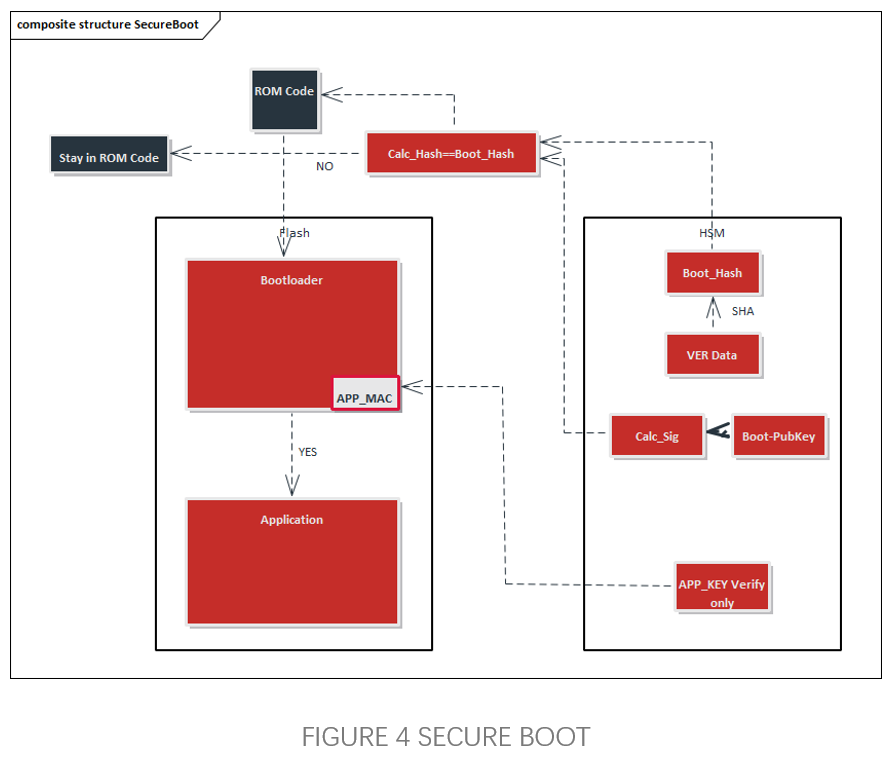
CYT4BB uses RSASSA-PKCS-v1_5 (2048bits Key) to read the Public Key pre-stored in SFLASH and the Signature value in Code Flash when the CM0 core is powered on and started up, and then through the pre-programmed RSA Verify interface integrated in SFLASH, it computes the Boot_Hash and Calc_Hash, which are compared to determine the reliability of the secure boot root of trust. Afterwards, the CM7 core is started for the verification of the secure boot trust chain. The first stage bootloader is verified by the root of trust code, and successful verification allows this to verify valid software execution and continue to verify the validity of software in subsequent boot stages.
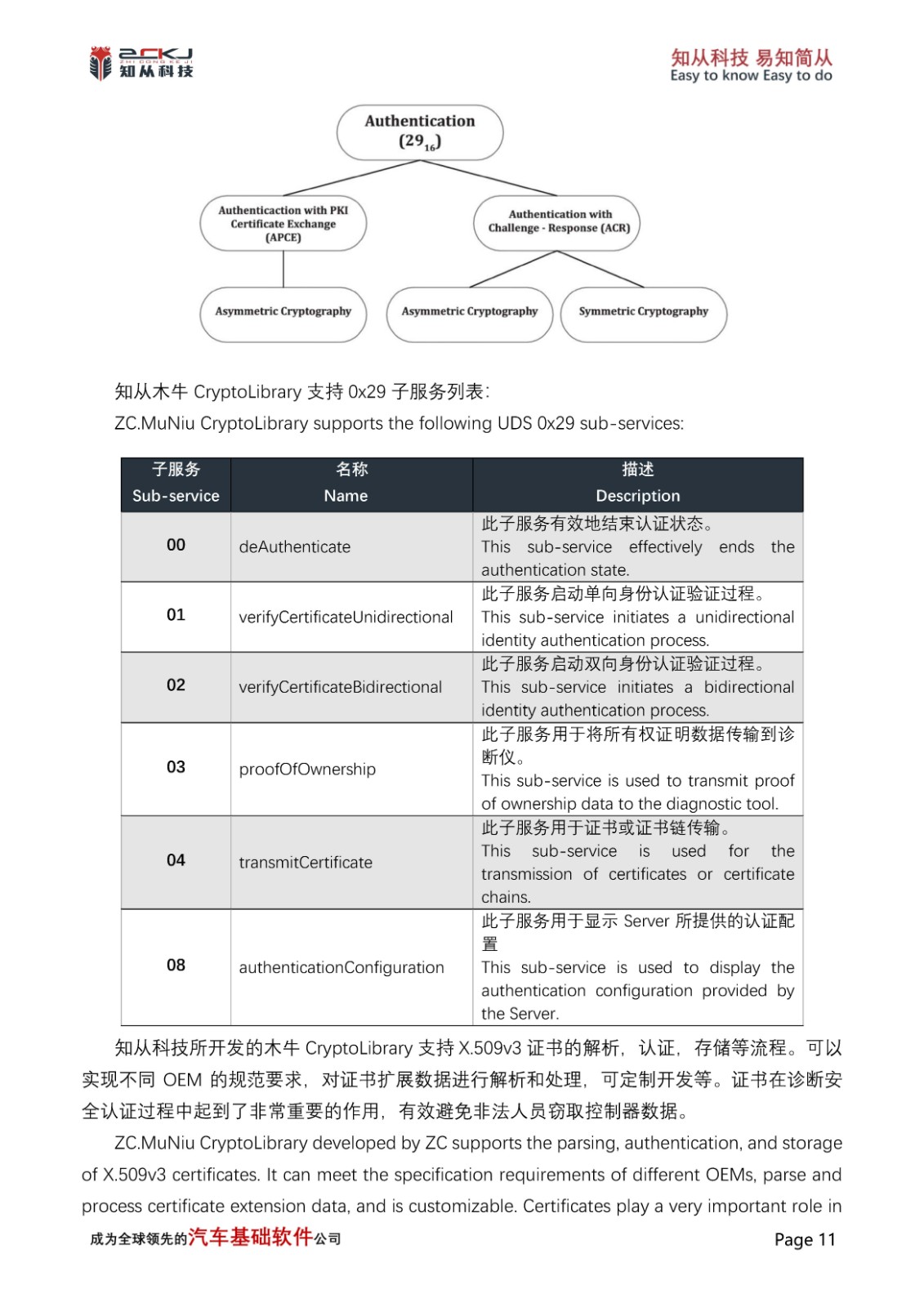
3 SECURE DIAGNOSTICS
Secure Diagnostic is an important means of protecting the internal data security of ECUs (Electronic Control Units). It is primarily used for diagnostic services that require identity verification when programs or data are downloaded/upload to a server and when specific memory locations are read from the server. Unusual program uploads or downloads to the server could potentially damage electronic devices or other vehicle components, or may violate vehicle emission or safety standards. On the other hand, when retrieving data from the server, data security could be compromised. Therefore, it is necessary to require the upper computer to prove its identity before executing these services, and only after legal identity confirmation is allowed to access data and diagnostic services.
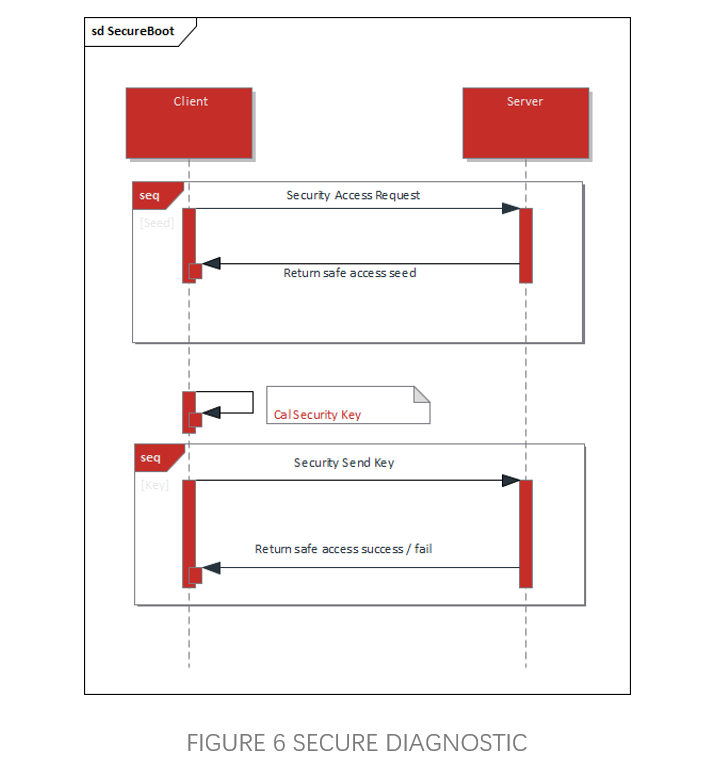
CYT4BB uses various hardware encryption algorithms such as TRNG/PRNG, AES128/256, AES-CMAC, HMAC, etc. to confirm the identity of the client and decide whether the client is allowed to access. The keys used for AES, CMAC, HMAC and other algorithms can be stored in advance using the LoadKey interface, and processed on the CM0 side by means of KeyID call, which ensures the reliability of the authentication information.
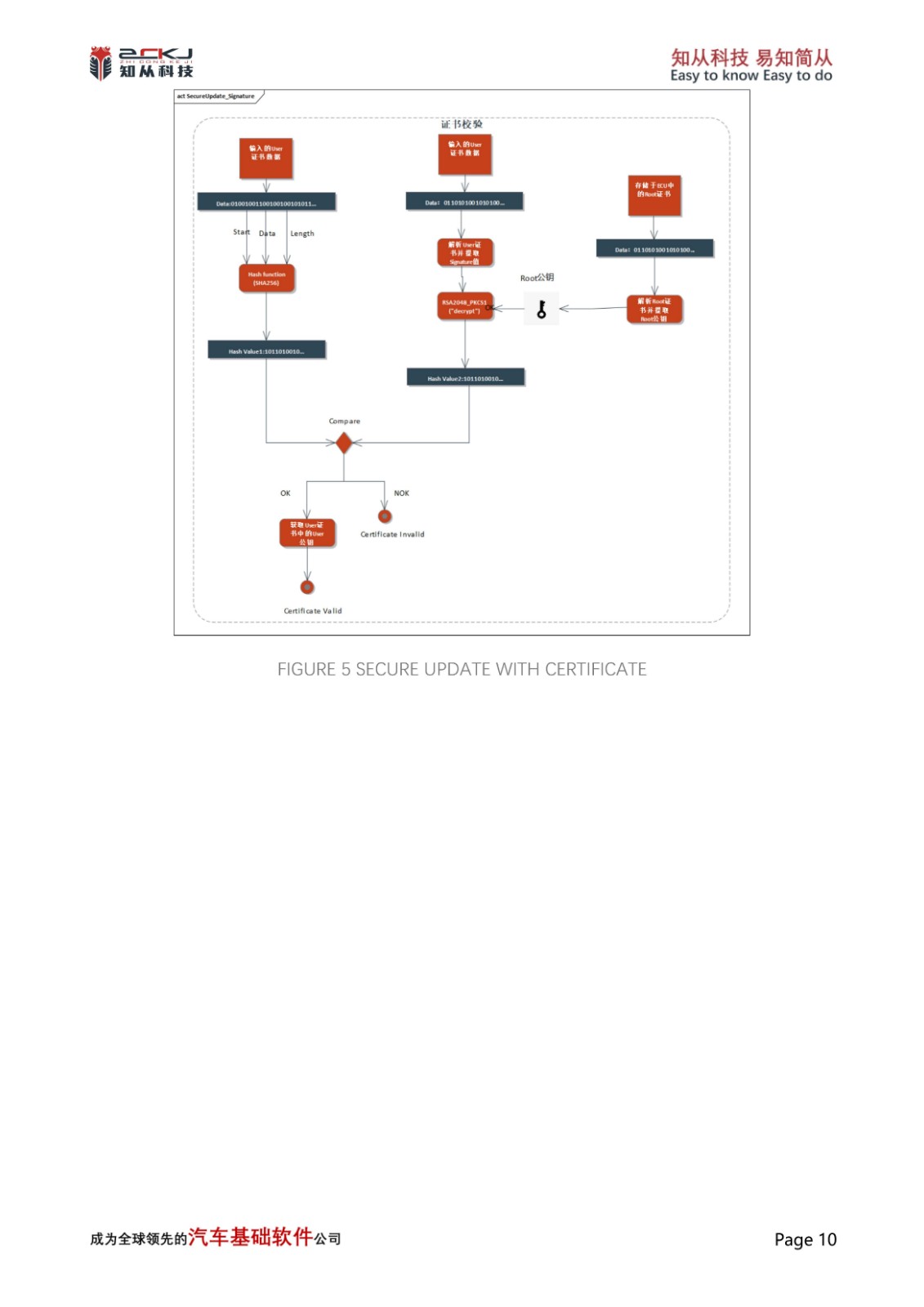
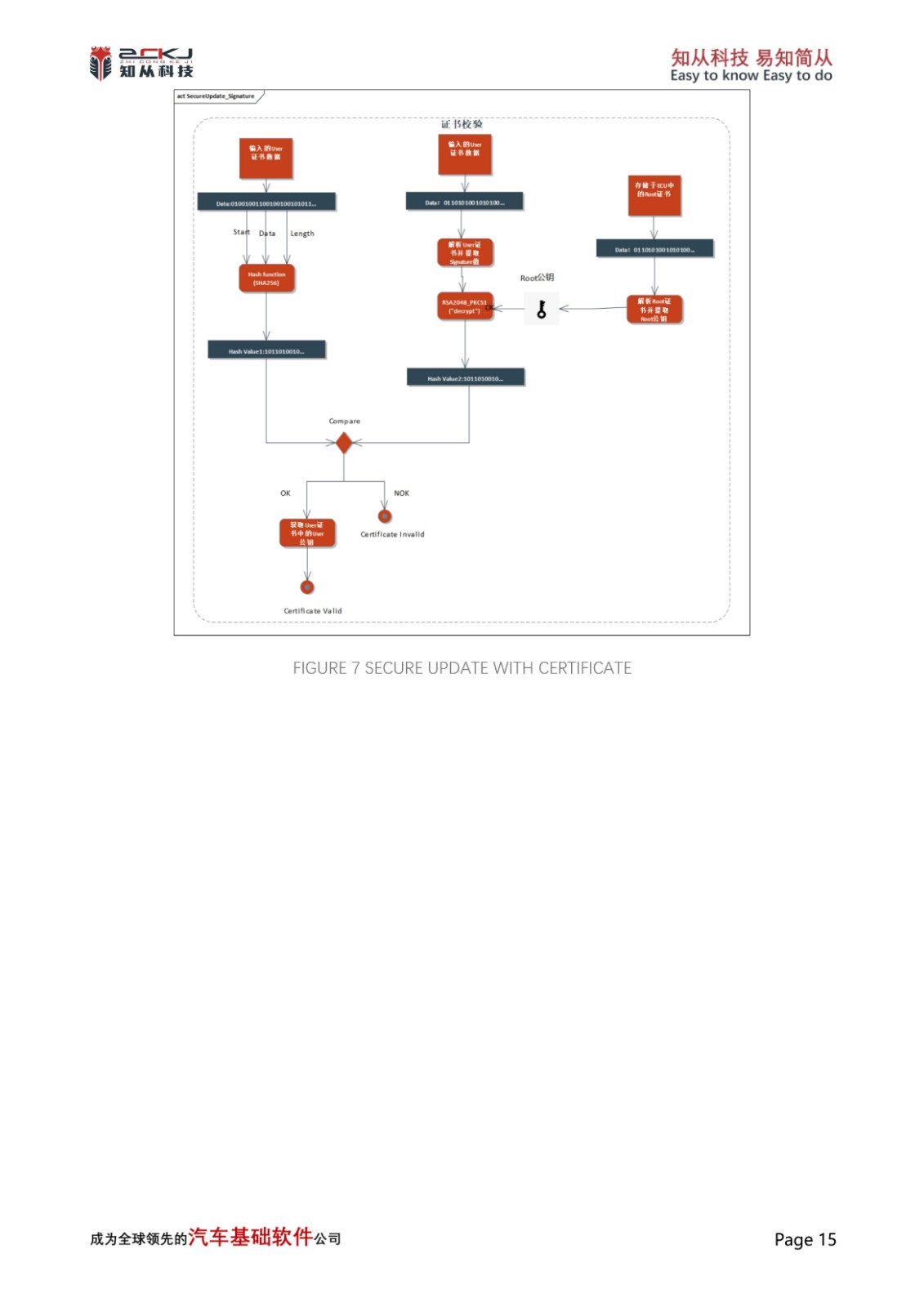
4 SECURE UPDATE
As network environments become increasingly complex, ensuring that the release source of upgrade packages is valid, not tampered with, data is not lost, and upgrade content is not maliciously obtained during the software upgrade process is becoming more and more important.In traditional upgrade processes, the upgrade package data is essentially transmitted in plaintext, and the data verification method is also a less secure CRC algorithm.
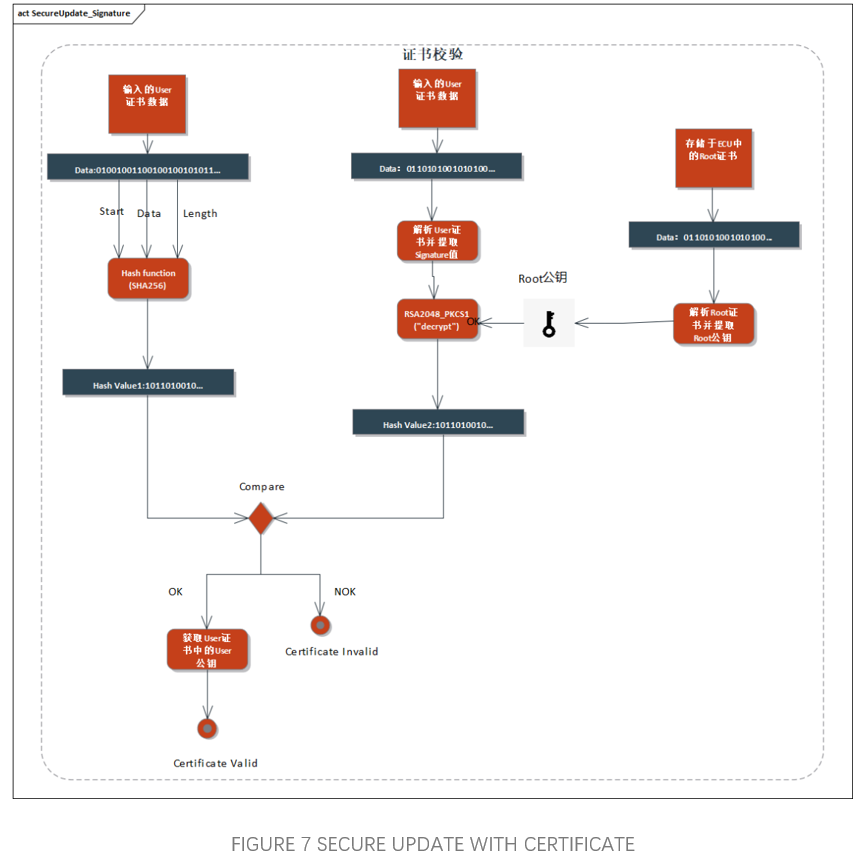
On the one hand, CYT4BB can adopt the RSASSA-PKCS-v1_5(2048/3072bits Key) algorithm that comes with its CM0 core, and on the other hand, it can also adopt Ed25519, ECDSA 256R1, RSASSA-PKCS-v1_5(4096bits Key), RSASSA-PSS-(4096bits Key), and so on, which can satisfy the user's needs for multiple algorithms. Key), RSASSA-PSS-(4096bits Key), etc., which can meet the user's needs for multiple algorithms. Moreover, for the PublicKey and PrivateKey used by the asymmetric algorithms therein, the same LoadUserKey interface can be used to pre-store them in the specified location of SFLASH and invoke them through the KeyID, which ensures the authenticity and integrity of the security upgrade process.
In addition, CYT4BB also supports certificate storage, which can call CM0 core Srom related interfaces to store the required certificates in the corresponding location of the Work Flash, and through the X.509 certificate parsing call interface and configure the algorithms for the implementation of certificate-based security upgrade mechanism
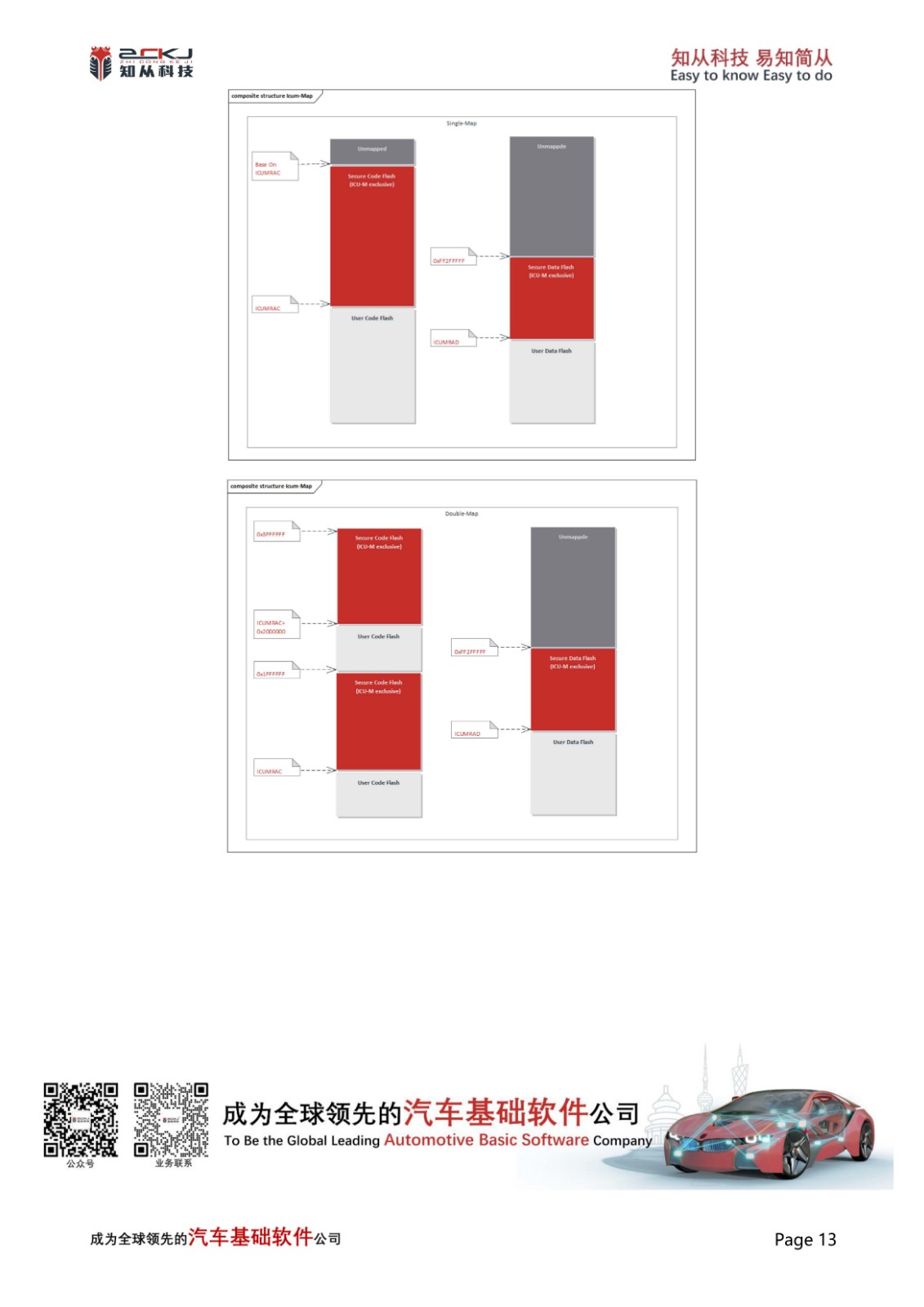
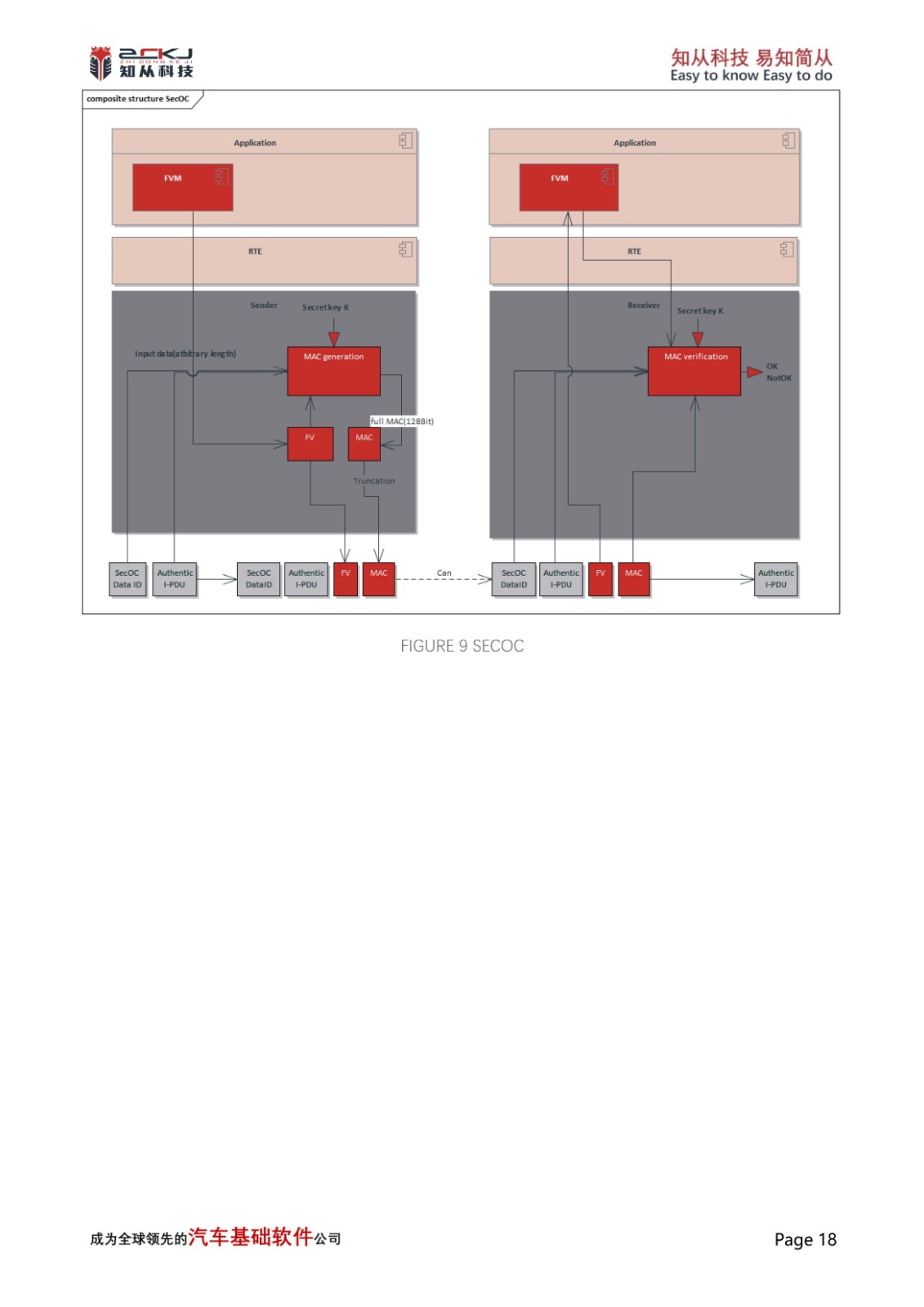
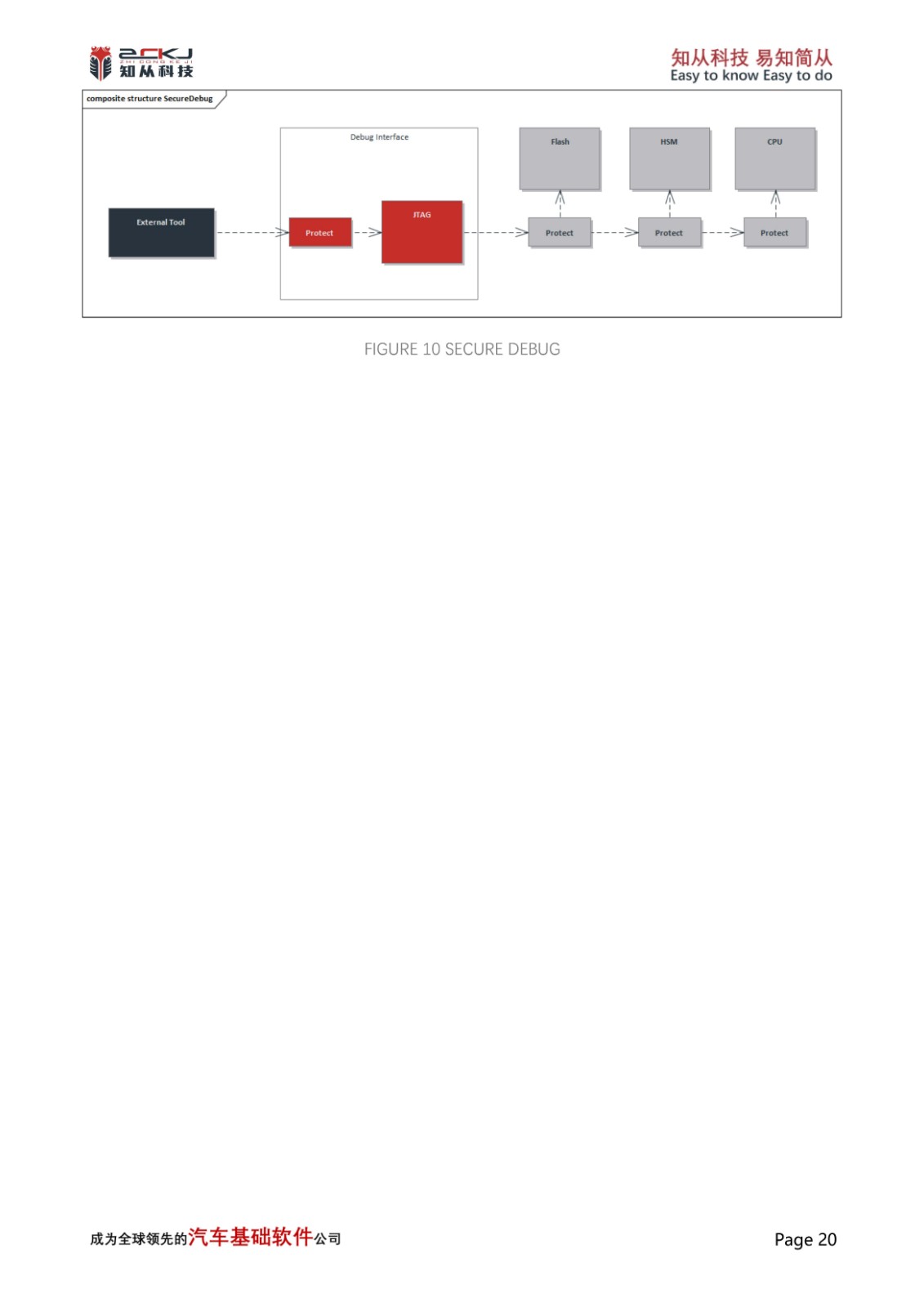
5 SECURE STORAGE
Secure Storage can protect the contents of data areas from being stolen abnormally, preventing the copying of stored keys, certificates, and other content due to forced access to the data storage area by controllers. Currently, mainstream chips can protect data by setting up Flash, Nvm, RAM, and other storage areas. Activating this feature can effectively prevent the aforementioned situations
CYT4BB achieves the foundation of secure storage by designating an internal SFLASH area for key and user information storage. On this basis, CYT4BB implements the secure storage of SHE key in accordance with AUTOSAR_TR_SecureHardwareExtensions specification, and encrypts and protects the key deposited in SFLASH to ensure the reliability of secure startup, secure diagnosis, and secure upgrade functions.